Memory Card
Partitions
Memory Card can be accessed with SceMsif module. It has the following partitions:
| code | type | name | desc |
|---|---|---|---|
| 0xD | raw | Some data | |
| 0x8 | exfat | ux0 | Memory Card |
mediaid partition
Findings about Memory Card
It turns out that memory card supports standard Memory Stick protocol (TPC).
Msif driver allows to read and write single values on memory card according to the (TPC) protocol.
It can also read and write chunks of data from memory card using (TPC) protocol.
It is still not confirmed, however based on some findings in Msif driver, it is hypothesized that Vita`s memory card is simply new generation of memory stick with additional auth layer. These findings include:
- Support of TPC protocol
- Msif driver contains code that can handle
Model Name Device Information Entry(In attribute area of the card). This code clearly shows that standard Memory Stick should be supported. - Dump of real memory card shows, that
Attribute Information Area Confirmation Structureis valid.
Memory Card Initialization
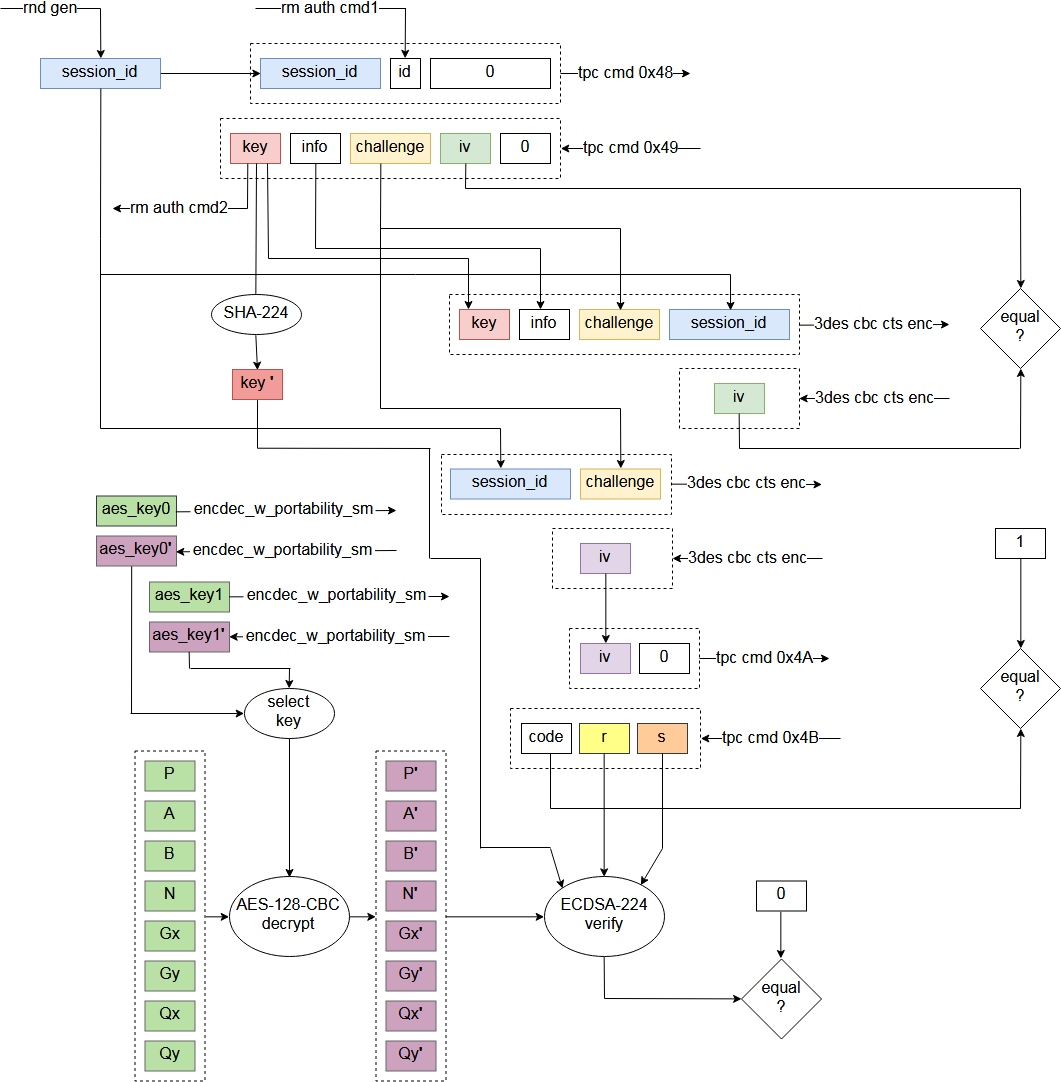
Much like SD standard allows execution of vendor specific commands through CMD56, Vita's memory card has specific commands 0x48, 0x49, 0x4A and 0x4B.
To be able to read from memory card, it has to be properly initialized with commands 0x48 and 0x49 first.
It is not completely tested yet, but commands 0x4A and 0x4B are probably not required, and used by Vita to check that memory card is genuine.
Memory card initialization also uses F00D rmauth_sm.self services 1 and 2.
Service 1 is used to obtain some data from F00D (1 byte).
Service 2 is used to set key, that is obtained from memory card, into slot 0x1C of SceSblDMAC5DmacKRBase keyring.
For encryption during memory card auth SceMsif driver uses 3-DES-CBC-CTS cipher.
Key that is returned from the card is unique to the card and is signed with ECDSA224 signature (custom curve).
This signature is verified by Msif driver.
Table of ECDSA224 parameters is stored in data section of Msif driver.
Table of ECDSA224 parameters is encrypted with AES-128-CBC (this still have to be doublechecked).
AES keys are stored in data section of Msif driver. There are multiple keys from which - one is chosen.
AES keys are encrypted. They are decrypted with F00D encdec_w_portability_sm.self service 0x2000A.
Faking memory card with hardware
Is not entirely possible. Reasons:
1. Private key for ECDSA-224 is unknown.
2. F00D keys used for corresponding service calls are not public.
Main problem is 1. In theory specific key and signature pair can be taken (dumped) and put into clone cards.
However they can be blacklisted in next firmware update.
Patching in software
Commands 0x48 and 0x49 are only used to verify that card is genuine. Data, given from card is used to calculate IV and compare it with IV that is calculated by the card. This can be removed by patching.
Command 0x4A is used by card to verify, that vita is genuine. Another IV is computed and sent to card to initialize it. This unlocks all I/O operations. This can be removed by patching.
Command 0x4B is used by vita to verify that card is genuine. This is done by checking the card key that is signed with ECDSA-224 signature. This can be removed by patching.